Projects & evidence
SAEs, internship and apprenticeship, with argued evidence
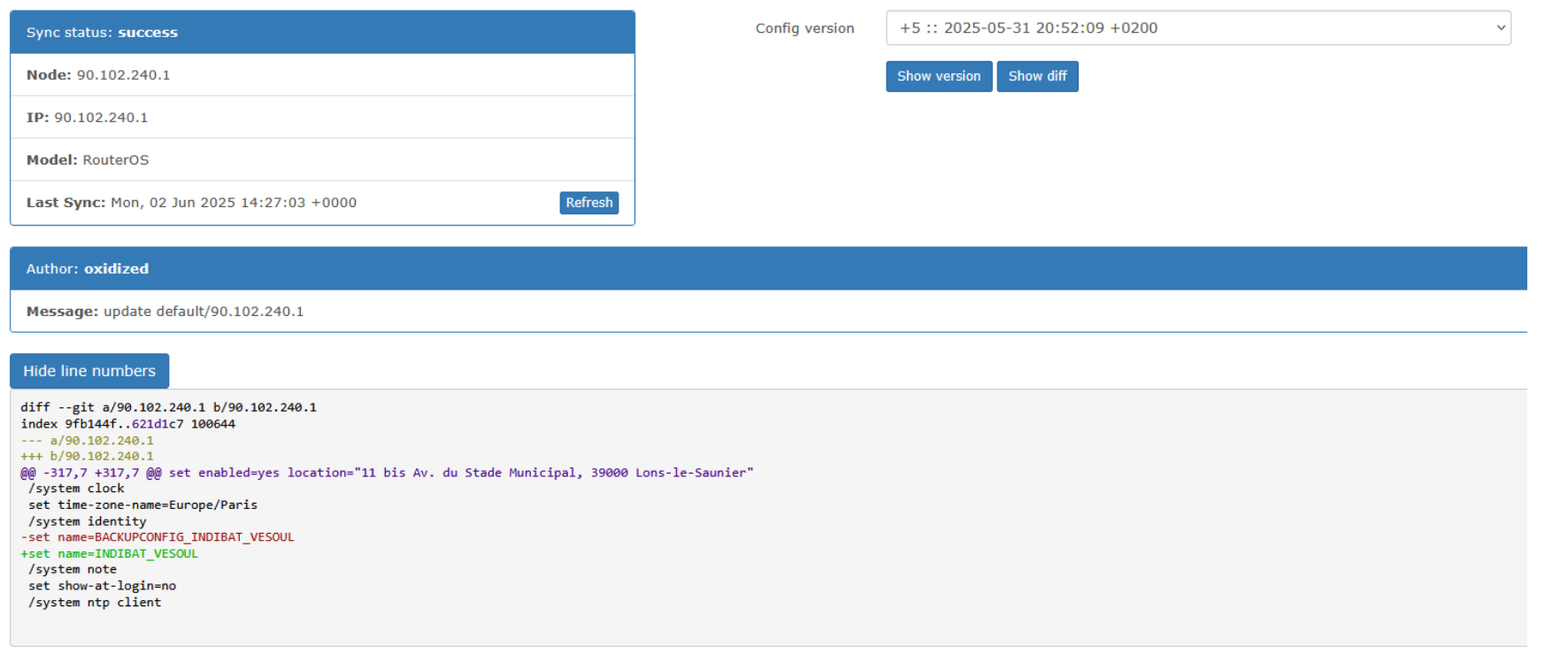
Oxidized — Network config backup & versioning
Deployed Oxidized to automate network device configuration backups, keep a full history via Git, and integrate monitoring into LibreNMS.
details:
Network config automation project – Oxidized implementation
As part of my training, I deployed an automated solution to back up and track network device configurations, with the goal of improving reliability through centralized storage, traceability, and version history.
This project focused on real operations concerns: change management, preventing configuration mistakes, and easing maintenance workflows.
- Deployed Oxidized on a dedicated Linux server and configured it.
- Connected devices over SSH, organized by groups and types.
- Automated config backups with full version history (diff/versions).
- Ops-oriented approach: traceability, troubleshooting, rollback.
This implementation improves infrastructure reliability and change tracking while reducing human-error risk.
Screenshot showing the integration and visibility in LibreNMS.
More docs
Automated deployment of switch configurations
Context: 100+ switches with a common baseline but per-device parameters (VLAN, IP, DNS, SNMP, uplinks…). Automated via a Python script over serial console.
details:
Switch deployment & configuration project – Operations and rollout
I carried out a switch deployment project focused on rollout, configuration, and integration into a secure and structured enterprise-like network.
It covered real operational constraints: initial setup, segmentation, security hardening, and maintainability.
- Initial setup: identity, admin access, SSH, hardening.
- Segmentation: VLANs, access/trunk ports, consistent network plan.
- Ops best practices: standardization, documentation, clarity.
Beyond configuration, the goal was long-term operability: consistency, easier troubleshooting, and progressive monitoring integration.
It strengthened my switching and device administration skills with a rigorous, operations-focused approach.
Script: Day0 init, generic config, custom parameters, interface config, save. (Secrets/IDs redacted).
Open script ↗More docs
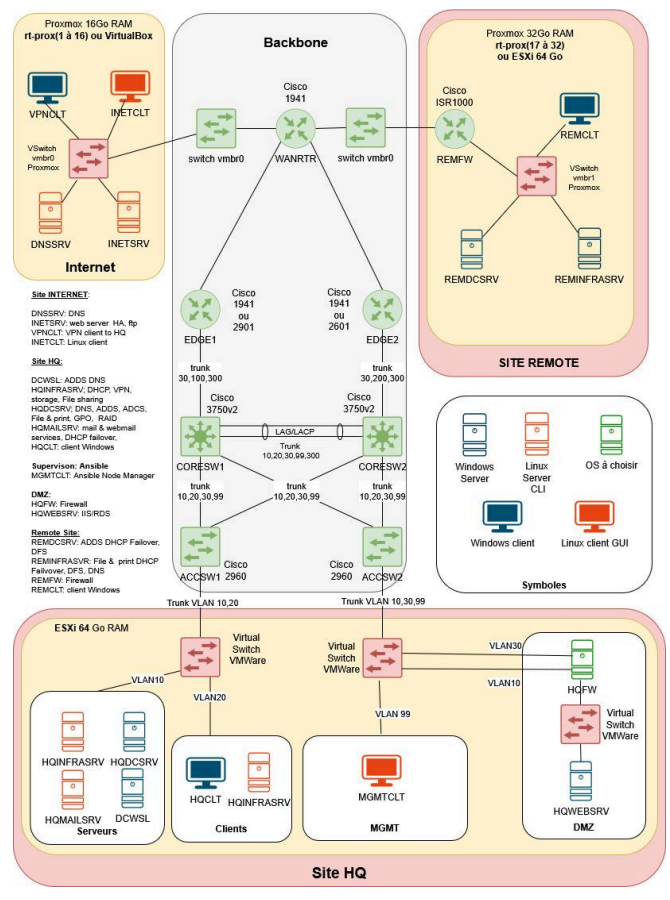
SAE 501 — Connecting companies and users
Design and deployment of a complete multi-site infrastructure: addressing, VLAN, routing, services (DNS/DHCP…), remote access, monitoring, and segmentation (DMZ/MGMT).
- Multi-site architecture (HQ / remote / backbone) + interconnections.
- Addressing plan + VLANs (clients, servers, MGMT, DMZ) + trunks.
- Routing & gateways (inter-VLAN, Internet access, routes).
- Network services (DNS/DHCP) and server roles per zone.
- Security: segmentation, DMZ, filtering principles, MGMT isolation.
- Monitoring/operations: run logic and service continuity.
details :
SAE 501 – Design, deployment and presentation of a technical solution
As part of SAE 501, our team designed and deployed a multi-site network infrastructure for a fictional company (HQ, remote site, Internet access).
Although the topic was assigned, it was a strong learning opportunity, reinforcing both technical skills and team coordination.
- Advanced segmentation (VLAN, DMZ, management) and multi-site interconnection.
- Protocols & services: dynamic routing, addressing plan, DHCP/DNS.
- IT services: Active Directory, GPO, web/mail, file sharing, backups.
- Security & monitoring: filtering, log collection, monitoring and alerts.
Personally, it was challenging due to workload and unexpected issues, but very rewarding technically and collaboratively.