Welcome
Academic portfolio (BUT Networks & Telecommunications)
Overview
A quick view to understand who I am and what’s inside this portfolio.
I’m a 3rd-year BUT Networks & Telecommunications student. This portfolio gathers my skills, projects (SAEs), and evidence (scripts, configs, docs) as part of an assessed approach.
- Goal: demonstrate my skills clearly and with justification.
- Content: projects, micro-learnings, skills and contact.
Timeline
Studies, internship and apprenticeship (summary).
My education
BUT Networks & Telecommunications — cybersecurity track: hands-on skills, evidence, and reflection.
BUT Networks & Telecommunications — cybersecurity-focused track
A program mixing technical skills (networks, systems, virtualization, monitoring, automation) and transversal skills (professional communication, rigor, documentation). Each semester, I rely on projects (SAEs), internship and apprenticeship to produce evidence and explain it.
Competency-based approach
The BUT program is competency-based: I must demonstrate real-world ability (projects, configs, scripts, reports), explain my decisions, and reflect on them.
- Concrete evidence (screens, repos, configs, docs) + rationale (context, constraints, decisions).
- A cybersecurity posture: hardening, access control, monitoring, traceability.
- A portfolio linking SAEs + apprenticeship + internship to show progression.
Targeted competencies
Key vocabulary (BUT R&T framework)
See CE and AC (Cybersecurity track)
- balancing security requirements and usability constraints
- respecting standards and the legal framework
- integrating the latest technologies
- working as a team
- effectively raising user awareness
- ensuring continuous watch and applying critical updates
- automating tasks
- integrating within a team
- monitoring network behavior
- ensuring contract compliance and information system obligations
- AC34.01Cyber — Actively contribute to a risk analysis to define a security policy for a small organization
- AC34.02Cyber — Implement advanced tools to secure a network infrastructure
- AC34.03Cyber — Secure operating systems
- AC34.04Cyber — Propose a secure information system architecture for a small organization
- AC35.01Cyber — Monitor information system activity
- AC35.02Cyber — Apply a penetration testing methodology
- AC35.03Cyber — Respond to a security incident
- AC35.04Cyber — Administer information system monitoring tools
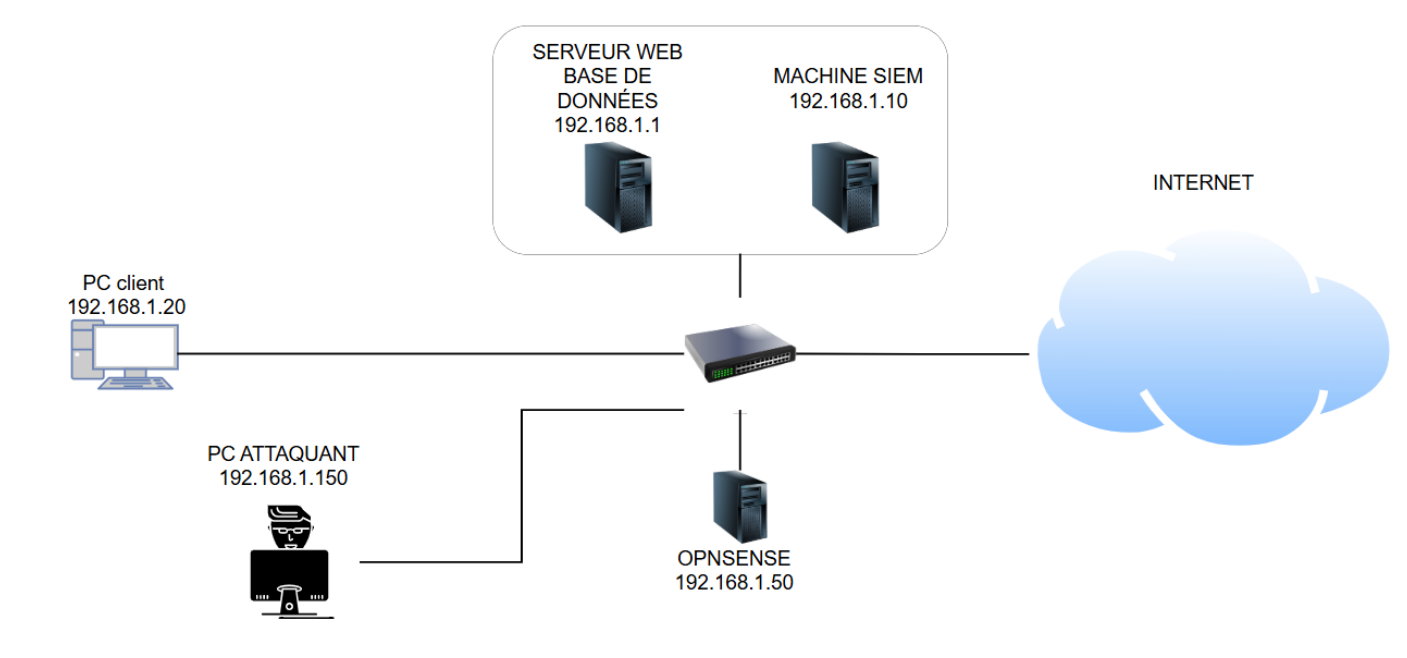
- As part of a team, I deployed a network and implemented full monitoring using log analysis and an Intrusion Detection System (IDS) to identify anomalies.
More detailed technical report:
Open PDF↗Professional experience
Concrete work from internship / apprenticeship.
Internship — Oxidized
Using Oxidized to back up and version network device configurations.
→ See Micro-learning for the dedicated video.
Apprenticeship SDIS25
Ongoing: large-scale switch deployment (scripting and on-site rollout), maintenance of radio, telephony, and network infrastructure.